TikTok app comes with a host of security concerns

This is part of a series of stories aimed at examining the role social media plays in the lives of teenagers.
January 12, 2022
This is the final story in our Social Media Illusions series. See here for full coverage.
It may not come as a surprise to hear that TikTok and its parent company Bytedance are a sketchy pair of companies. The Beijing-based company has engaged in numerous questionable activities in the past that violated user privacy.
On more than one occasion, TikTok has used malicious techniques and exploits in order to gain user data. One example is when TikTok used an unpatched Android security hole to obtain the user’s MAC address. A MAC address is a physical identifier given to wireless devices, mainly Wifi and Bluetooth in this case. MAC addresses are not completely unique, but it’s unique enough to the point where it can be an accurate identifier, which can prove useful in keeping track of collected user data and building a profile around a user. In addition, the hardware MAC address cannot be changed without special tweaks. MAC address tracking was banned by Apple in 2013 and Google in 2015.
Despite Google’s “banning” of the practice, an estimated 1% of Android apps did it anyway.
In 2020, iOS 14 received an update which gave users an alert when apps accessed their clipboard. TikTok, along with many other apps, were caught red-handed stealing clipboard data. Here’s a Youtube video showing TikTok copying clipboard data every few keystrokes. TikTok removed the “anti-spam” feature shortly after. Prior to the removal, any copied data, which could be passwords or other sensitive information, was viewable by TikTok, and was likely sent to their servers.
TikTok seems to be an obsession over device identifiers. Here is some of what TikTok admits to collecting in their privacy policy: IP address, mobile carrier, time zone settings, advertising IDs, device model, network type, SIM data (IMEI), OS info, GPS location, installed apps, battery state, keyboard input, audio settings, and many other bits of data.
None of those require user consent.
IMEI is a unique number given to mobile phones to identify them on cell networks. IMSI is a number assigned to mobile subscribers, and will move across a user’s devices. Neither of those numbers can be changed, not legally at least. An IMEI can tell what exact device model you have and is not something you’d want public. IMEI changing is definitely possible, but it’s considered identity theft and can result in jail time. Because of its uniqueness, it serves as the perfect way to track users. TikTok collects IMEI data as part of its SIM data extraction, and according to the security analyst group Penetrum who reverse-engineered the app, IMSI is likely to be collected as well, but that is not with complete certainty.
TikTok has a few different ways of getting a user’s location. TikTok, along with many other apps, can access a user’s GPS location without consent. On iOS, this is permitted to an accuracy of three decimal points, which can be accurate down to a couple hundred meters. IMEI and IMSI information can also be used to determine the user’s country. The user’s IP address is collected and logged, which can reveal location and a user’s identity on the internet. Apps and sites collect IP addresses all the time, however, most don’t have elaborate data mining and selling schemes. Advertising identifiers and time zone settings can also be used to reveal the user’s location.
When you take a photo on your phone, a file is created for that image. However, that file contains more than the image itself. Images like PNGs and JPEGs store metadata using the Exif format. Details include the GPS location of the photo, the camera that took the photo, the date and time, the focal length, and a lot more info which you can view here. Any app where you upload media taken by your phone will be able to see all this information.
Modern web browsers have a feature called “Do Not Track”, which serves as a way to let sites know that a user does not want to be tracked. Some sites respect this setting, some don’t. TikTok blames the differences in how browsers implement the setting for its absence from the platform. This is true, there is not a consistent implementation for Do Not Track. However, it is not difficult to implement and only takes a little bit of Javascript.
TikTok sends all the data it collects to its servers across the world, an estimated 37.7% of which are located in China, according to the cybersecurity research company Penetrum. Most data transfers between client-side apps and servers use REST APIs, which uses the HTTP protocol to get the job done. Today, practically all API calls have basic encryption using HTTPS and TLS, which protects against basic attacks (like packet sniffing on a LAN). However, until May 5, 2020, TikTok was using basic, unencrypted HTTP for their API calls. A company, Mysk Inc, demonstrated the severity of this vulnerability by modifying the data packets that were being received to show different content. This is not a simple mistake in the slightest. This represents a disregard for security, an incompetency of the developers, or both.
TikTok’s privacy policy is vague about where exactly user data is sent. TikTok says they do sell personal information to third parties. However, they do share personal information with “service providers and business partners.” This includes payment processors, cloud providers, tech support providers, but also advertisers.
“Advertising, marketing, and analytics vendors, who may receive the information you choose to provide, the information we obtain from other sources, and the information we collect automatically but would not receive your payment information or message data.” The next clause states the following, “We may share all of the information we collect with a parent, subsidiary, or other affiliate of our corporate group.” This means that TikTok is within its rights to share data all across its parent companies and subsidiaries.
Let’s do a quick overview of the corporate structure of TikTok’s parent company, Bytedance.
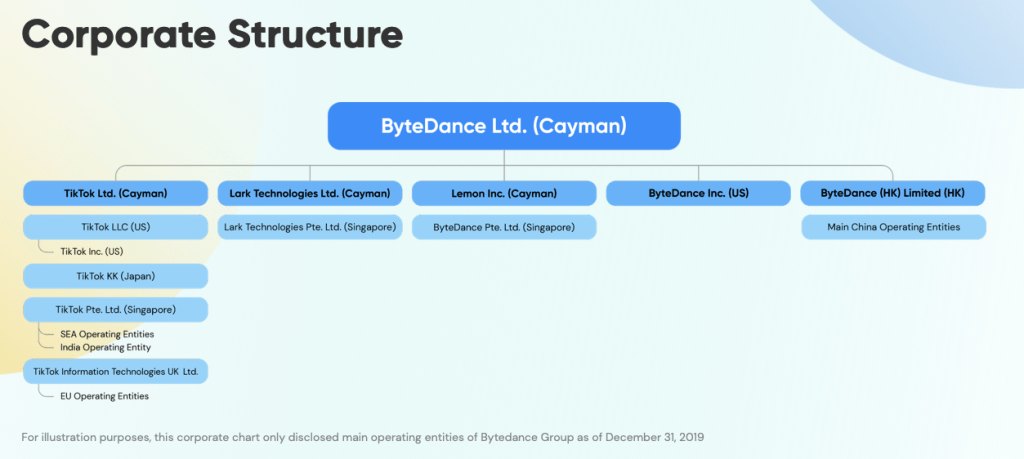
Bytedance was founded in the Cayman Islands in 2012. It has several parent companies, including TikTok and Bytedance subsidiaries that operate in different jurisdictions. Bytedance currently has its global operation headquarters in Beijing, China, with various offices across the world. TikTok denies the ability of the CCP to access user data. However, because Bytedance operates out of China, it is subject to 2017 National Intelligence Law, which states that “any organization or citizen shall support, assist and cooperate with the state intelligence work in accordance with the law.”
In June 2020, a cybersecurity research group known as Penetrum published their security and privacy focused research on TikTok, which included a partial reverse engineering of the app. Reverse engineering is a method to find the original source code from which an app binary was built, in this case TikTok’s Android apk. This was used to reveal the APIs that are used to fetch user data from the OS and what type of practices TikTok uses in their code. Keep in mind that this research was conducted on a version of TikTok from 2020, so it is likely that some things have changed since then. Even if the code changed, the point is that TikTok implemented these things in the first place and it is a violation of user privacy.
I already mentioned that TikTok uses unencrypted HTTP for their API calls and what risks that brings above. The app uses MD5 hashes throughout the app, which has been deprecated since 2011. A modern hash such as SHA-512 should be used instead (this will likely make people laugh in the future). TikTok passes commands to its local SQLite database using user defined variables, which can pose the risk of an SQL-injection attack. Sanitization of user defined variables is a basic security practice. The fact that TikTok does not sanitize their queries simply shows the incompetence of their developers. Android WebView is a way for app developers to display web pages within their app. When used properly, it is a useful tool. TikTok ignores SSL/TLS errors in its use of WebView, which can allow for malicious sites to take the place of what was actually supposed to be loaded. However, the main concern is how TikTok enables remote debugging and uses user defined commands.
As Penetrum puts it, “anyone who figures out how to enable and leverage this capability of this app, can use it or execute man in the middle attacks.” The use of remote debugging in a situation like this can allow something as bad as remotely running malware to occur.
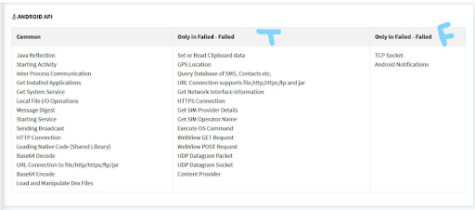
Penetrum compared TikTok’s privacy practices to Facebook and Twitter. Penetrum compared the API calls used by both apps found from the reverse engineering. Below is an image that shows the APIs used by both TikTok and Facebook (left), only TikTok (center), and only Facebook (right).
Below is an image of the same comparison but with Twitter instead of Facebook.
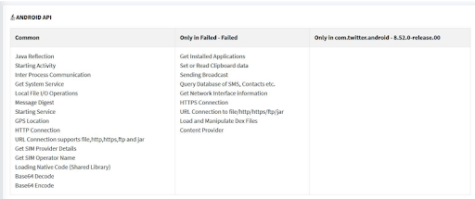
In both situations, TikTok used far more APIs, many of which were likely used to collect user data.
It’s worth mentioning that in November 2021, TikTok settled a class action lawsuit over the collection and usage of biometric user data. The settlement totaled to $92 million, and anybody who used TikTok or Musical.ly before Sept. 30, 2021 is eligible for a payment. Illinois users are eligible for six times the payment, linked here by the US District Court for the Northern District of Illinois.






